Blogs
Home / Blog


When you start a cybersecurity program in your organization, you might come across numerous challenges. Add to that the number of things you need to take care of, and it will make the task even more challenging. From application security to cloud security, encryption to network security, everything is your responsibility.
Throw in some strict regulatory requirements and it is enough to give your IT team some sleepless nights. Thankfully, all is not lost. You can overcome most if not all of these challenges by using a cybersecurity framework.
A cybersecurity framework is a set of processes that is used to define policies and procedures related to information security controls in an enterprise. These information security controls help you identify, protect and recover from cyberattacks. It provides you a blueprint to create your own cybersecurity program based on your specific business needs.
In this article, we will look at some of the best cybersecurity frameworks and how it can help you secure your business.
These are seven cybersecurity frameworks that are worth considering for implementation.
COBIT stands for Control Objectives for Information and Related Technology. It is a cybersecurity framework developed by ISACA. This framework was designed to reduce the technical risk in organizations but later evolved into something that aligns your business goals with IT goals.
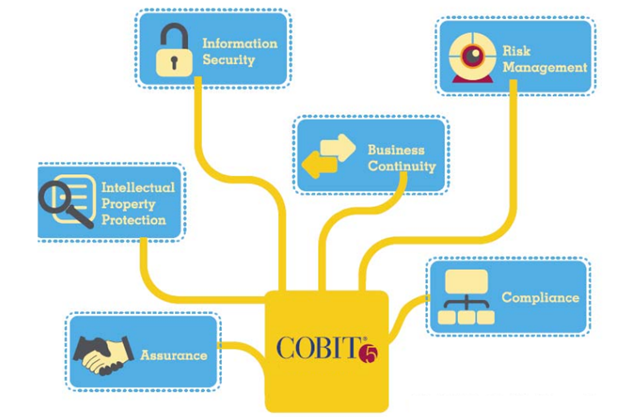
COBIT framework is an ideal choice for businesses looking to enhance the security and quality of production. It gives you end-to-end process control of the enterprise and helps in meeting stakeholders’ expectations. COBIT differentiates IT management from IT governance while offering a single integrated framework that can govern both.
NIST stands for the National Institute of Standards and Technology. This cybersecurity framework focuses on secure communication between external and internal environments and minimizes risk by implementing best practices and principles. What makes NIST stand out from other cybersecurity frameworks is that it can be implemented in any organization irrespective of its size and degree of cybersecurity risk.
There are five critical functions of NIST:
By developing a better understanding of these core functions, you can improve the resilience and security of your organization.
For those looking for a comprehensive cybersecurity framework that covers all bases, ISO 27000 series is a great option. Developed by the International Standard Organization, this IT security framework can be applied to all types of organizations. For the ease of understanding and implementation, it has been divided into many sub-standards with each sub-standard dealing with a specific domain.
For instance, ISO 27001 clarifies the requirements while ISO 27002 focuses on operational steps needed to implement this information security program. Work on new sub-standards is underway which would deal with the emerging challenges such as cloud security, digital evidence collection and storage security. Whether you want to secure data stored on your database, best-dedicated servers or cloud, it will have you covered.
CIS critical security controls is a long list of technical controls, best practices and configuration. It focuses more on improving technical infrastructure minimize risk and make your business more resilient against cyberattacks. Its actionable operational advice and ability to work alongside other IT security frameworks makes it a great tool for mitigating risks.
Unlike NIST cybersecurity framework, CIS ignores risk analysis and risk management. If risk analysis or risk management is your priority, you are better off sticking with NIST framework. The long list of controls can prove to be of great help especially if your IT team lacks technical experience and knowledge.
PCI DSS stands for Payment Card Industry Data Security Standard is a combination of security standards designed to ensure that companies that accept, process, store or transmit credit card payments maintain a secure environment so that the credit card information of users stay safe. This standard was designed to minimize credit card fraud.
PCI DSS has 12 requirements that a business should comply with to become PCI-DSS compatible.
COSO is the Committee of Sponsoring Organization. It mainly focuses on monitoring, controlling, auditing and reporting risks. This framework has 17 core points which have been divided into five different components:
All these core concepts are combined to create policies that can suit your business requirements. Users can tweak the framework according to their business structure so it can benefit their operational units.
HITRUST CSF stands for Health Information Trust Alliance Common Security Framework. This IT security framework is designed for the health care industry. Most organizations avoid this framework and there are many reasons for it. Obtaining and maintaining HITRUST certification is costly and requires more effort as it demands extensive documentation and refined processes. Its strict criteria do not help either.
On the brighter side, it borrows requirements from every compliance regulation you can think of and offers a comprehensive framework which can be implemented in any organization this is even beyond the realm of healthcare. HITRUST not only deals with risk analysis and risk management but also covers operational requirements as well.
Which cybersecurity frameworks do you implement in your organization? Let us know in the comments section below.
Enter your email to receive the latest news, updates and offers from HostNoc.
