Blogs
Home / Blog

According to cloud access security broker statistics, the cloud access security broker market has grown exponentially during the last four years. It went from $870 million in 2019 to a whopping $3.8 billion in 2023. This clearly shows the exponential growth in the cloud access security broker market.
If you are heavily invested into the cloud ecosystem but don’t know much about cloud access security brokers, you are missing out on the control and security that a cloud access security broker brings to the table. Don’t worry. Because you have landed on the right article.
In this article, you will learn about everything you need to know about cloud access security brokers.
Cloud access security broker is a software or hardware that is either hosted on the cloud or an on-premise system and acts as a mediator between cloud service providers and its users. This allows it to identify and fix loopholes present in different cloud models such as software as a service (SAAS), platform as a service (PAAS) or infrastructure as a service (IAAS).
Additionally, it even empowers organizations to expand the security policies already implemented on on-premise systems, to cloud infrastructure. This allows businesses to safely use cloud environments without worrying about putting their sensitive business data at risk.
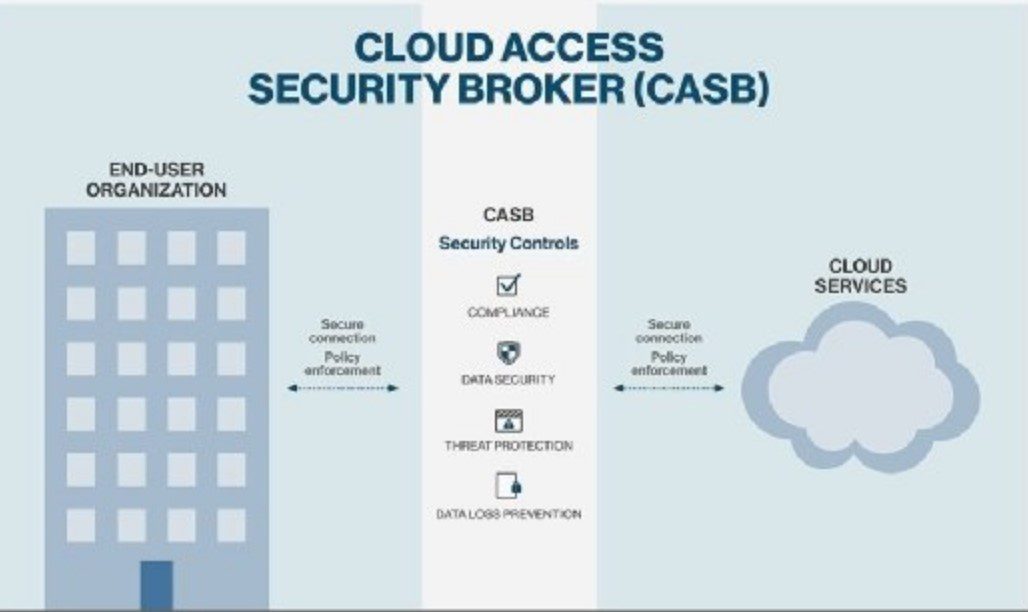
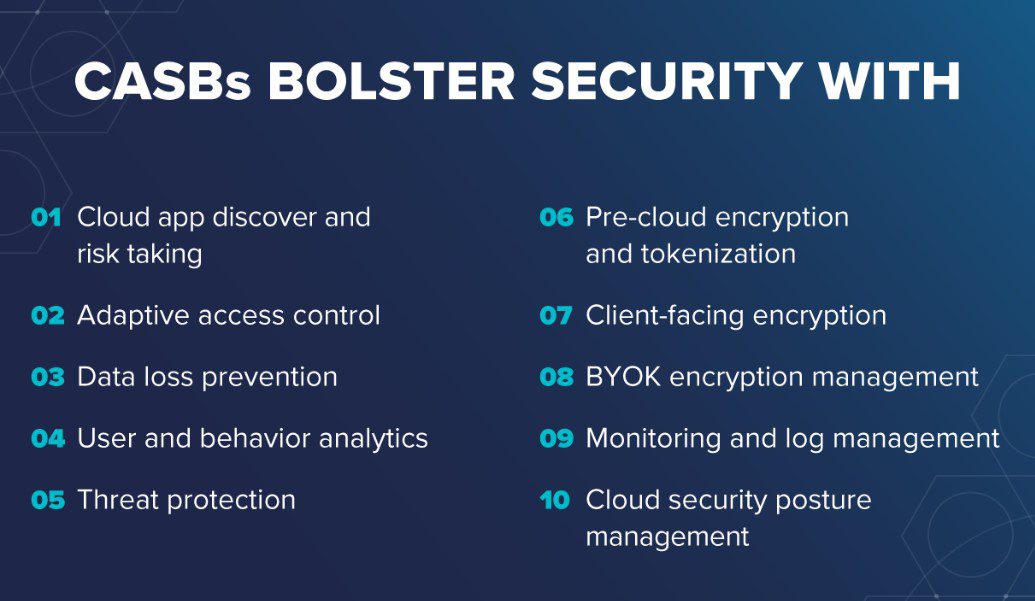
Now that you know what a cloud access security broker is, let’s look at how it actually works. Cloud access security broker acts as a firewall, overseeing data flowing to and from the cloud architecture and cloud vendor environments. Its core objective is to secure the data based on the organization’s security policy.
Even though there are numerous use cases and applications for cloud access security brokers, there are a few popular instances. One of them is to monitor and secure the shadow IT. It is also used to safeguard sensitive business and user data from getting leaked or stolen.
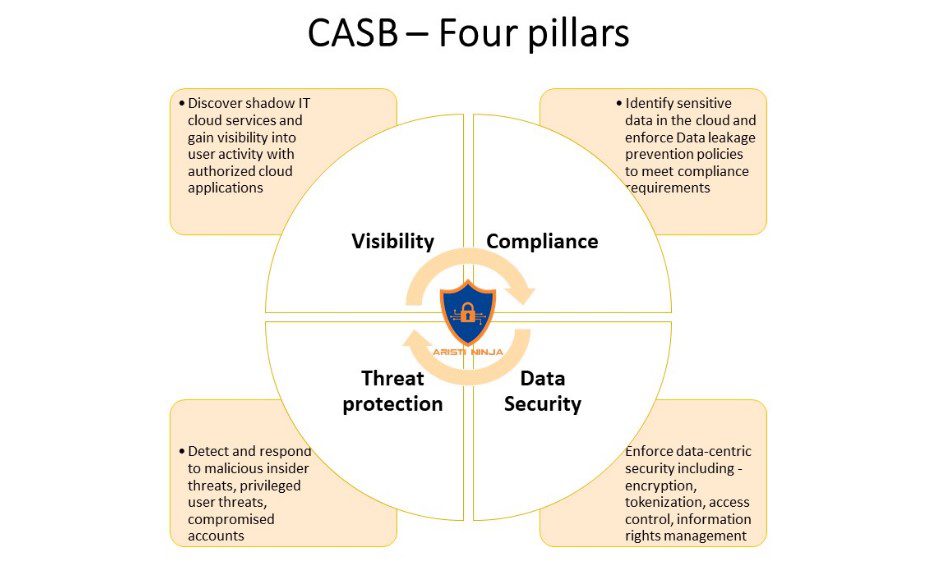
A cloud access security broker has four key pillars.
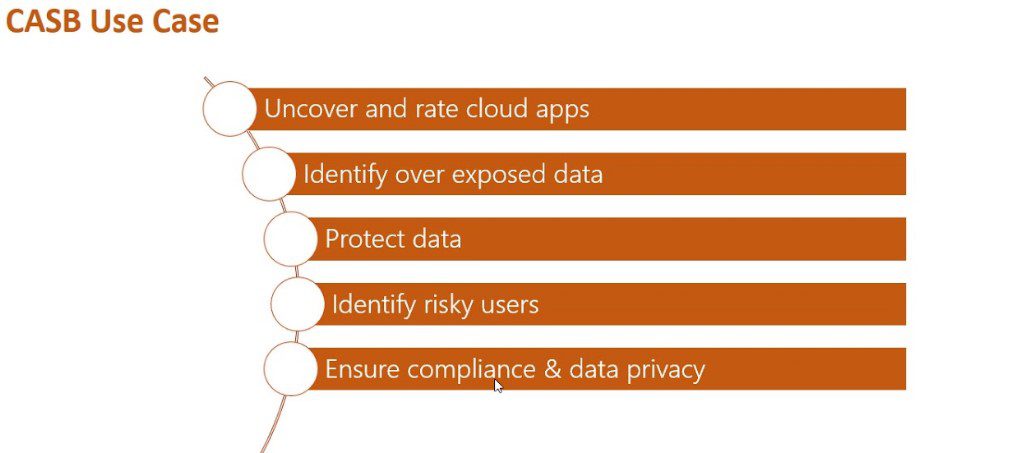
There are five key advantages of cloud access security brokers:
Let’s look at each advantage in more detail to give you a better idea.
Although a majority of businesses have already adopted cloud infrastructure or are migrating from on-premise systems to cloud, the number of cyberattacks targeting the cloud has grown tremendously in the last few years. By implementing a robust cloud access security broker solution, you can minimize those risks substantially.
A good cloud access security broker solution not only allows businesses to monitor user behavior, but also lets you control data accessibility. In addition to this, you can also keep an eye on all the devices connected to your network and control which files are being shared externally, and with whom. This goes a long way towards reducing the risk of cyberattacks, and minimizing the risk of business disruptions, reputation damage and financial losses.
Most cloud access security broker solutions have a separate module for protecting your data. The data loss prevention module actively enforces cloud security policies and limits user activities to keep risk of data breaches in check. Due to this, threat actors are thwarted from fulfilling their malicious desires and your data stays safe and secure in the cloud.
Users can apply restrictions based on geolocation, accessibility and time. Moreover, it puts you in the driver ‘s seat when it comes to granting permission to users. The best part is that all this is applicable on both data in motion and data at rest, which provides complete protection to your data stored in the cloud.
Privilege and admin accounts are the prime target for cyber attackers, since they can wreak more havoc on them as compared to traditional user accounts. Since these privilege and admin accounts have higher levels of access, once cyber criminals get their hands on these accounts, they can do irrevocable damage.
As a business, your goal is to prevent that from happening. The best way to do that is to use a cloud access security broker. It allows you to efficiently manage privilege and admin accounts and allows you to apply restrictions and grant permission.
One of the biggest advantages of migrating to the cloud is accessibility. You can literally grant access to your data stored in the cloud to anyone, which is great but also comes with security risks. Cloud access security brokers mitigate that security risk by letting you control everything when sharing files externally. You can keep unwanted guests at bay and prevent proliferation attempts by using access blocking features.
All cloud applications are not created equal. Some are more risky than others. Unfortunately, organizations don’t know much about vulnerable cloud applications and continue using them, which puts their data at a much greater risk. A cloud access security broker can facilitate your shadow IT operations and help you find the insecure cloud applications.
Not only that, it can empower your business to restrict access to those vulnerable applications. Even better, it even tells you about the users which are at the highest risk of being compromised. With all this information at your disposal, you can easily block threats to your users and applications. This also helps with complying with industry standards such as HIPAA and others.
Did this guide help you in understanding what CASB is and how it can benefit your business? Share your thoughts in the comments section below.
Enter your email to receive the latest news, updates and offers from HostNoc.
