Blogs
Home / Blog

In today’s rapidly evolving digital landscape, Cloud Security computing has emerged as a transformative force, offering organizations unmatched scalability, flexibility, and cost-efficiency. However, amidst the boundless possibilities of the cloud, there loom critical security challenges that demand our immediate attention. Enter the thought-provoking survey conducted by SUSE, the pioneering open source software provider.
This insightful study has shed light on the very real cloud security hurdles that businesses face today. So, fasten your seatbelts as we embark on a captivating journey through these challenges, unraveling strategies to fortify cloud security. By tackling these obstacles head-on, we can unlock the immense potential of the cloud while fortifying the fortress of our organization’s data and assets.
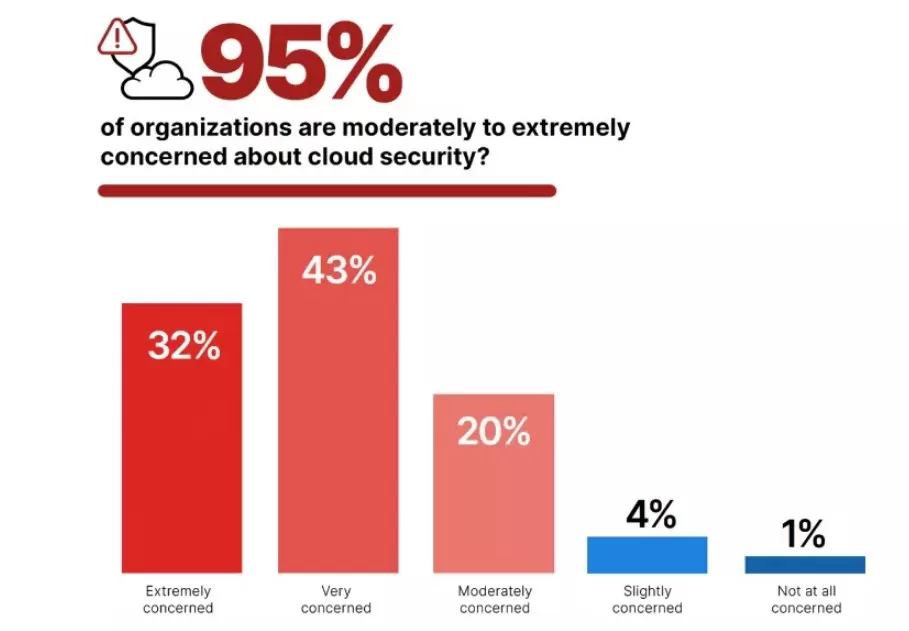
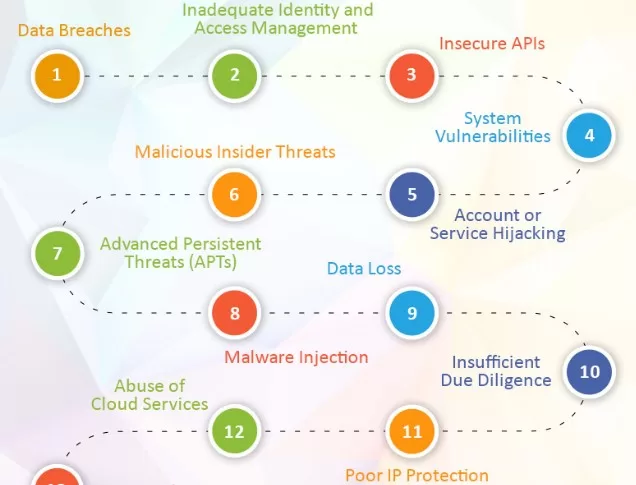
Here are top ten cloud security challenges, according to a survey conducted by SUSE.
Migrating to the cloud can reduce the organization’s visibility and control over security mechanisms compared to on-premises environments. This limited control can make it challenging to detect and respond to security incidents effectively. Implementing robust monitoring and logging systems, utilizing cloud-native security tools, and establishing clear responsibilities with the cloud provider can help address this challenge and enhance visibility and control over the multi cloud environment.
Implementing robust monitoring and alerting mechanisms enables organizations to detect potential issues or anomalies that may lead to data loss. This includes monitoring storage health, backup job completion status, and other relevant metrics. Timely alerts and proactive responses can help prevent data loss or minimize its impact.
Well-documented backup and disaster recovery procedures are critical for effective data protection and recovery. Organizations should maintain comprehensive documentation outlining step-by-step instructions, responsibilities, and escalation paths.
This documentation ensures that the recovery process can be executed efficiently, even during high-stress situations. By incorporating these elements into their backup and disaster recovery strategies, organizations can enhance their resilience in the face of potential data loss in the cloud. It is essential to regularly assess and update these strategies as technology evolves and business requirements change to ensure ongoing data protection and business continuity.
Establishing a comprehensive governance framework and risk management strategy is essential. It includes defining policies, procedures, and controls to manage security risks associated with cloud adoption and continuously monitoring and assessing these risks.
Relying on managed cloud service providers means trusting their security practices. Organizations need to assess the security posture and certifications of cloud providers to ensure they meet industry standards and adequately protect customer data.
Insider threats refer to the risk posed by individuals within an organization who have authorized access to the cloud environment but may misuse or leak sensitive data intentionally or unintentionally. Organizations need to implement stringent access controls, monitoring mechanisms, and employee awareness programs to mitigate the risk of insider threats.
Different industries have specific compliance and regulatory frameworks (e.g., GDPR, HIPAA) that govern how data should be handled and protected. Organizations must ensure their cloud environment meets these requirements, including data privacy, data residency, and security controls, to avoid legal and financial consequences.
Proper access control mechanisms should be implemented to restrict access to interfaces and APIs based on the principle of least privilege. User roles and permissions should be defined, and access to sensitive data or functionalities should be carefully controlled. Regular review and revocation of access rights for users and applications that no longer require access are critical to minimize the attack surface.
Implementing robust logging and monitoring for interfaces and APIs allows organizations to detect and respond to any suspicious or malicious activities promptly. Logs should capture relevant information, such as API requests, responses, error messages, and user identities, for effective forensic analysis and incident response. Real-time monitoring and alerting mechanisms help identify unusual patterns or anomalous behavior, enabling proactive mitigation of potential threats.
Effective management of the API lifecycle includes version control, deprecation planning, and regular updates to address security vulnerabilities and introduce new security features. It is crucial to stay up to date with security patches and updates provided by API vendors or maintainers. Organizations should also have a plan in place to deprecate and retire older, insecure API versions to avoid exposure to known vulnerabilities.
Cloud computing involves the sharing of physical infrastructure among multiple users. If a vulnerability exists in the underlying infrastructure or hypervisor, it could potentially impact the security of all tenants. Organizations should thoroughly evaluate the security practices of their cloud provider, including patch management, network segregation, and isolation mechanisms, to reduce the risk of shared infrastructure vulnerabilities.
Managing user identities, authentication, and authorization across multiple cloud models, services and platforms can be complex. Organizations need robust identity and access management solutions to ensure only authorized individuals have access to sensitive data and resources.
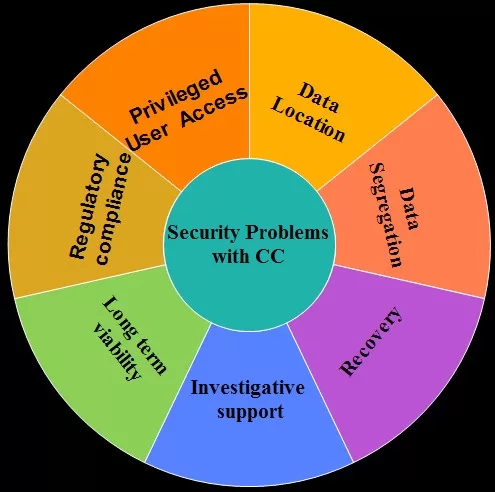
Protecting data in transit and at rest is crucial in the cloud. Encryption, data classification, and data privacy controls must be implemented to safeguard sensitive information from unauthorized access and ensure compliance with data protection regulations.
Organizations operating across multiple regions may face challenges related to data sovereignty and compliance with local data protection laws. Understanding where data is stored, processed, and transmitted in the cloud is crucial to ensure compliance and address potential legal and regulatory issues.
IT leaders bear the crucial responsibility of navigating the treacherous terrain of cloud security. The SUSE survey has equipped us with a treasure trove of insights into the specific threats that lurk in the cloud. Armed with this knowledge, we can forge ahead with confidence, embracing robust identity and access management, bolstering data protection measures, ensuring regulatory compliance, and adopting comprehensive risk management strategies. Let us not forget to stay vigilant, keeping a watchful eye on the security practices of our cloud providers and nurturing a responsive incident response capability.
Enter your email to receive the latest news, updates and offers from HostNoc.
